What is Decentralization?
Decentralized networks are made up of computers, also known as nodes, that interact on a direct, peer-to-peer basis, without the need for third parties. Within a decentralized network, information is distributed to every single “node” on the network. Each node has an updated copy of all recorded data. Decentralized networks can also distribute data so that certain private information can be validated without that information being transferred to a third party. Data is validated by using an agreed-upon consensus mechanism, which often involves the other computers on the network checking the validity of the data before it becomes permanently imprinted onto a blockchain.
Did you know?
Decentralization was first proposed as a military technology during the cold war. Despite this, most internet services and even public utilities are still highly centralized systems.In a decentralized network, each participating node is independent of the others. Rather than following the instructions of a central authority, decentralized nodes connect using common rules, but maintain their sovereignty and manage their own privacy. This helps keep the network secure, while also ensuring relatively democratic governance.
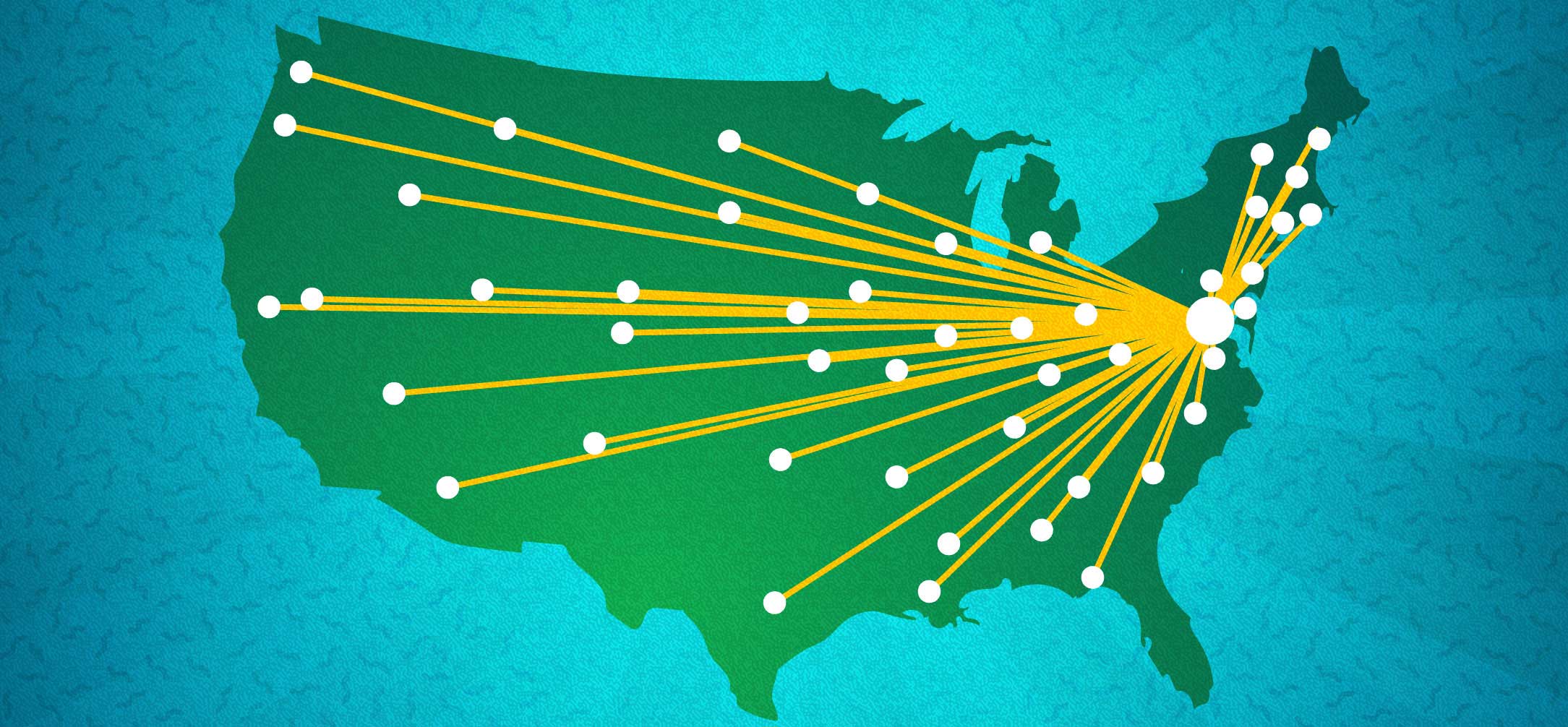
Centralized
Centralization occurs when a system relies to heavily on a small number of relay nodes. This can lead to reduced stability if the core nodes are mismanaged.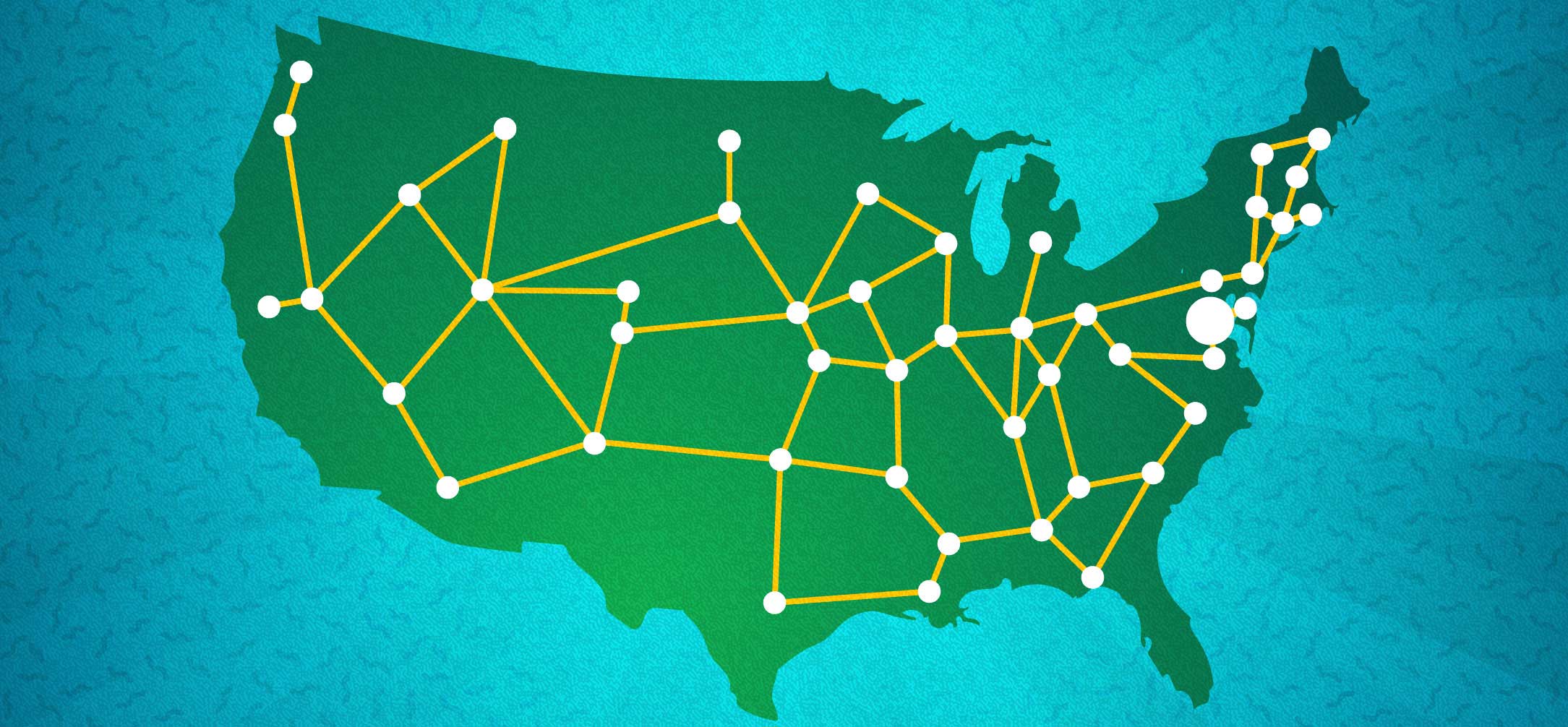
Decentralized
A system is decentralized if it's partipants are able to connect either directly (Peer to Peer) or through a network of nodes which are not centrally managed. Most blockchains are decentralized networks.A consensus mechanism is a way for nodes to come to an agreement about the validity of data before it becomes part of a blockchain. Once the block contains this data, it is distributed among nodes, making it near impossible to change data that has already been recorded to the ledger. Instead of changing data in one centralized database, changing the data on a decentralized network, a majority of nodes would have to be updated to reflect fraudulent information within a short amount of time for that information to be adopted by the other, uncorrupted nodes. Otherwise, such information will be rejected by validating nodes.
Learn More
For more information on this topic please visit our Decentralized Storage course.